Passkey Management
The Passkey Management feature in Veeam Kasten provides an interface for managing encryption passkeys used to securely encrypt and decrypt the primary Kasten encryption key responsible for protecting backup data. This feature allows administrators to create, view, and manage multiple passkeys from different key management stores via both the Kasten UI and kubectl commands.
Overview
These passkeys use envelope encryption to protect the primary Kasten key used to derive keys for all application backup data and metadata. The primary key performs the encryption of backup data, while passkeys encrypt and protect the primary key itself.
A passkey is considered valid when Kasten can successfully access and use it to decrypt the primary key. Invalid passkeys may result from issues connection to external services, missing Kubernetes secrets, or other configuration errors.
Each Kasten instance requires a minimum of one valid passkey to function. It is not possible to delete the last remaining valid passkey.
Veeam Kasten supports the following types of passkeys:
- Passphrase: Uses a passphrase specified in a Kubernetes Secret
- AWS Key Management Service: Uses AWS Customer Managed Keys (CMK)
- HashiCorp Vault: Uses Vault Transit Secrets Engine
- Azure Key Vault: Uses Azure Key Vault Keys
Passkey Management Via the UI
Admin users can view all valid passkeys under Settings > Passkey Management. This allows you to see all valid passkeys for Kasten.
Create a Passkey
- Create New Passkey: Click the "Create New Passkey" button
- Configure Passkey Details:
- Passkey Name: Enter a unique name for the passkey
- Passkey Type: Select from AWS Key Management Service, HashiCorp Vault, Azure Key Vault, or Passphrase
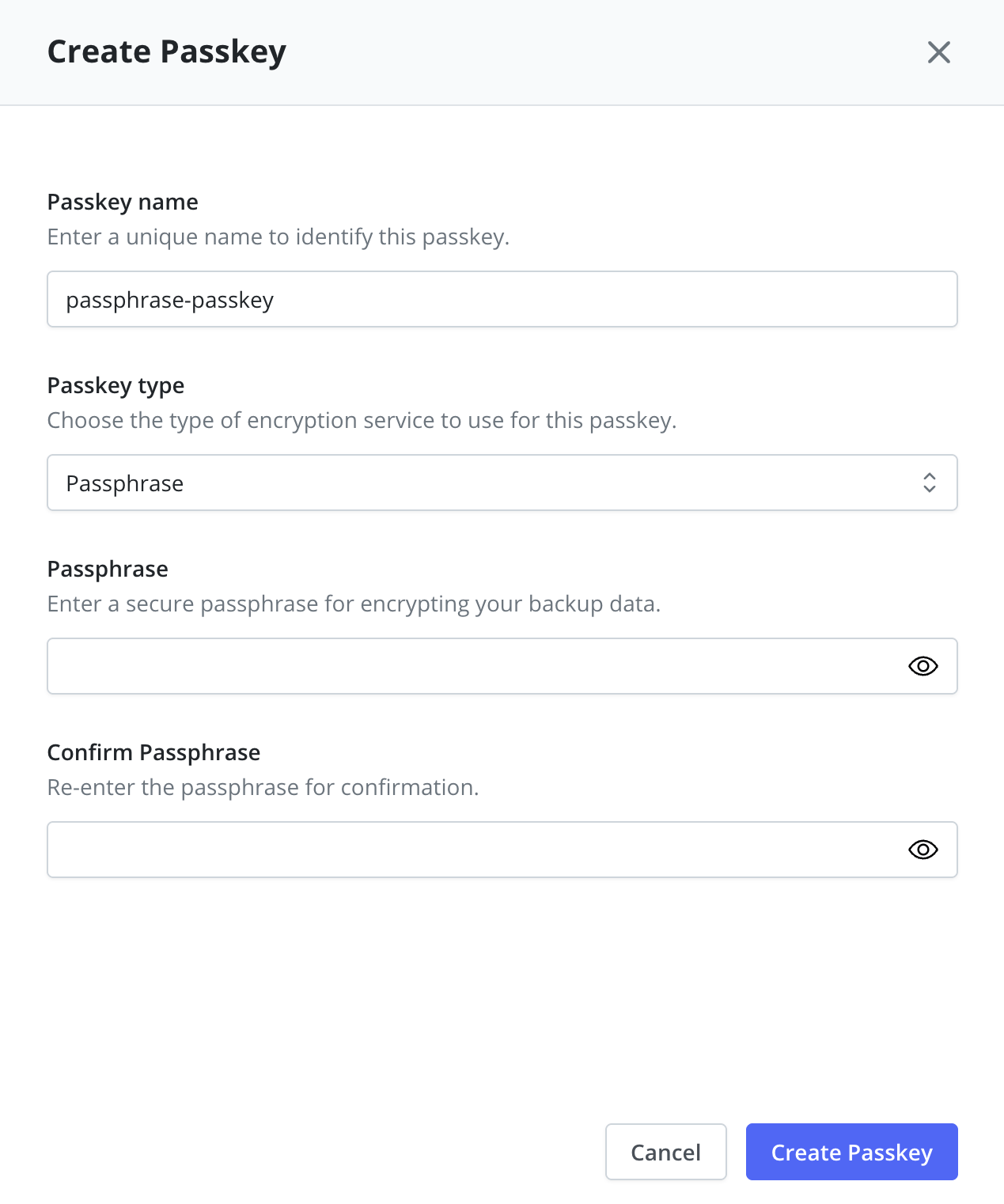
Passphrase Configuration
- Passphrase: Enter a secure passphrase for encrypting backup data
- Confirm Passphrase: Re-enter the passphrase for confirmation
Store the passphrase securely outside of the cluster, as it will be required for disaster recovery operations.
Passphrases are less secure than using a managed key service like AWS Key Management Service, Azure Key Vault, or HashiCorp Vault.
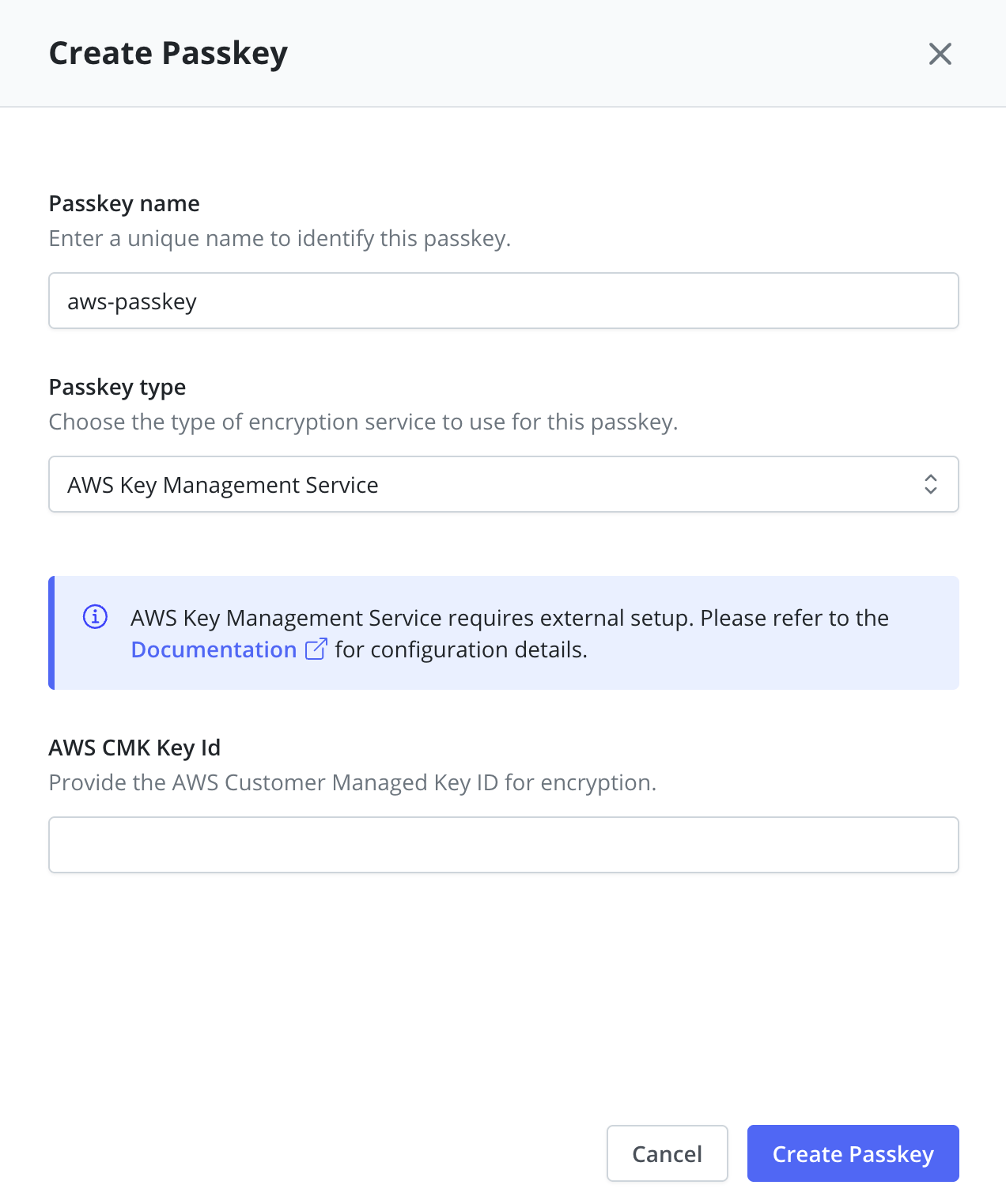
AWS Key Management Service Configuration
- AWS CMK Key ID: Provide the AWS Customer Master Key ID
- Format:
arn:aws:kms:region:account:key/key-id - Example:
arn:aws:kms:us-west-2:111122223333:key/1234abcd-12ab-34cd-56ef-1234567890ab
- Format:
Using AWS Key Management Service requires that an AWS Infrastructure Profile exists with the required permissions
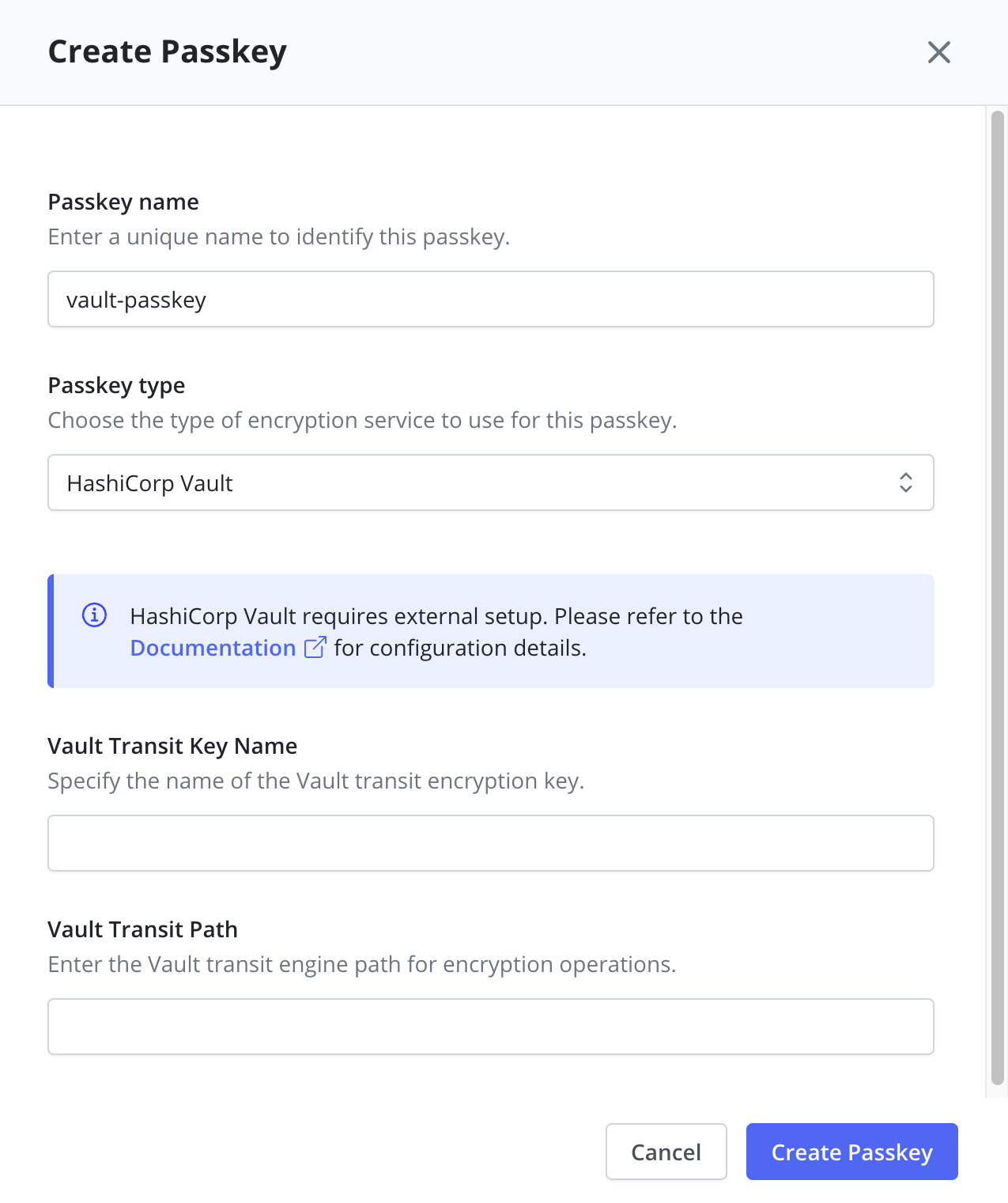
HashiCorp Vault Configuration
- Vault Transit Key Name: Specify the name of the Vault transit encryption key
- Vault Transit Path: Enter the Vault transit engine path for encryption operations
- Default path is typically
/transit
- Default path is typically
Using HashiCorp Vault requires that Veeam Kasten is configured to access Vault.
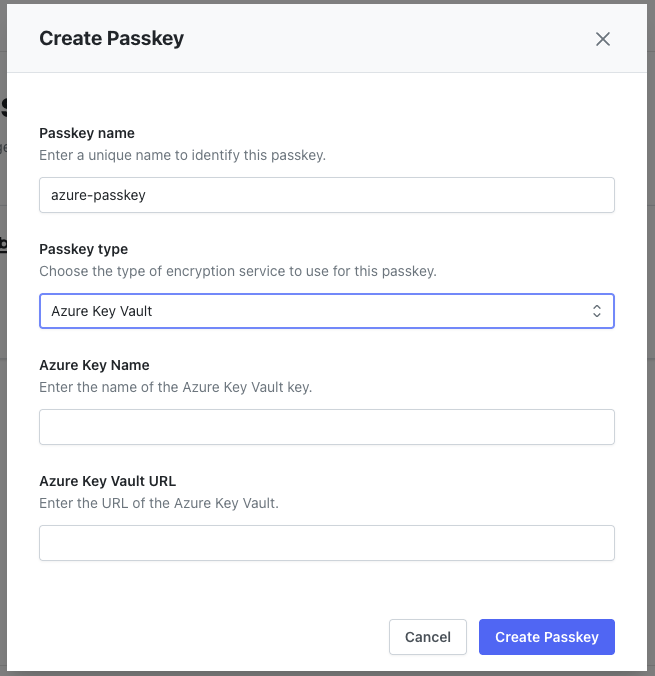
Azure Key Vault Configuration
- Azure Key Name: Provide the name of the Key in Azure Key Vault
- Example:
my-key-name
- Example:
- Azure Key Vault URL: Enter the unique URL to your Azure Key Vault
- Format:
https://<azure_keyvault_name>.vault.azure.net - Example:
https://my-vault-name.vault.azure.net
- Format:
To use Azure Key Vault with Kasten, you must configure Kasten with credentials that have the necessary permissions to wrap and unwrap keys. Example Role Key Vault Crypto Service Encryption User see Key Vault Roles for more information. These credentials can be provided in one of the following ways:
-
Azure Infrastructure Profile: Create an Azure Infrastructure profile in Kasten and provide credentials with the required Key Vault permissions.
-
Direct Secret Injection: During Kasten installation, set the
secrets.azureTenantID,secrets.azureClientId, andsecrets.azureClientSecretvalues to supply the required credentials. -
Azure Federated Identity: Alternatively, you can configure Kasten to communicate with Azure Key Vault by enabling Azure Federated Identity on your Azure Red Hat OpenShift (ARO) or Azure Kubernetes Service (AKS) cluster.
For details on configuring federated identity, refer to the Federated Identity configuration guide.
When Kasten creates a passkey using Azure Key Vault, it utilizes the latest available key version in the Key Vault at the time of creation. This specific key version is then associated with the passkey for its entire lifetime. If the key in Azure Key Vault is rotated, you must generate a new passkey to leverage the updated key version. The existing passkey will continue to be useable but will be based on the older key version. Please note that if the key version tied to an existing passkey is disabled in Key Vault, the corresponding passkey will become unusable.
Delete a Passkey
To delete a passkey via the UI, select the passkey and click the delete option. A confirmation popup will appear to confirm the deletion. Note that you cannot delete a passkey if there is only one passkey remaining, as each Kasten instance requires a minimum of one valid passkey to function.
Passkey Management Via the CLI
Passkeys can be managed programmatically using kubectl commands with the passkeys.vault.kio.kasten.io resource.
Creating Passkeys
Passphrase Passkey
A Passkey that represents a passphrase expects a Kubernetes Secret to be provided which contains the passphrase. This can be done via the creation of a Kubernetes secret in the Veeam Kasten namespace:
kubectl create secret generic <secret-name> \
--namespace kasten-io \
--from-literal passphrase=<key>
As shown below, this secret can then be used to create a Passkey. Note that Passkeys are non-namespaced.
cat > sample-passkey.yaml <<EOF
apiVersion: vault.kio.kasten.io/v1alpha1
kind: Passkey
metadata:
name: passkey1
spec:
secret:
## Reference to the passkey secret
name: <secret-name>
namespace: kasten-io
EOF
kubectl create -f sample-passkey.yaml
AWS KMS Passkey
A Passkey can also be used to represent an AWS KMS Customer Managed Key(CMK). The AWS CMK key ID can be provided directly in the passkey.
cat > sample-passkey.yaml <<EOF
apiVersion: vault.kio.kasten.io/v1alpha1
kind: Passkey
metadata:
name: passkey2
spec:
awscmkkeyid: arn:aws:kms:us-west-2:111122223333:key/1234abcd-12ab-34cd-56ef-1234567890ab
EOF
kubectl create -f sample-passkey.yaml
HashiCorp Vault Passkey
A Passkey can also be used to represent a HashiCorp Vault Transit Secrets Engine. The Vault Transit key name and mount path can be provided directly in the passkey, as shown below.
In addition, a vault authentication role and path to the service account token used for Vault's Kubernetes Authentication method can be passed in, vaultauthrole and vaultk8sserviceaccounttokenpath, respectively. This will override those values originally set via the helm install Kubernetes Auth.
If using Token Auth, passing in these two values will have the effect of upgrading the authentication method from Token to Kubernetes. Please ensure your vault server is properly configured as shown in Configuring Vault Server for Kubernetes Auth before adding these to the Passkey.
cat > sample-passkey.yaml <<EOF
apiVersion: vault.kio.kasten.io/v1alpha1
kind: Passkey
metadata:
name: passkey3
spec:
vaulttransitkeyname: my-key
vaulttransitpath: my-transit-path
vaultauthrole: my-auth-role
vaultk8sserviceaccounttokenpath: /var/run/secrets/kubernetes.io/serviceaccount/token
EOF
kubectl create -f sample-passkey.yaml
Azure Key Vault Passkey
A Passkey can also be used to represent an Azure Key Vault Key. The Azure Key Vault key name and Key Vault URL can be provided directly in the passkey.
cat > sample-passkey.yaml <<EOF
apiVersion: vault.kio.kasten.io/v1alpha1
kind: Passkey
metadata:
name: passkey2
spec:
azurekeyname: my-key
azurekeyvaulturl: https://my-keyvault.vault.azure.net/
EOF
kubectl create -f sample-passkey.yaml
Listing Passkeys
To list all Passkeys, simply run:
kubectl get passkeys.vault.kio.kasten.io
Getting Passkeys
To get a specific Passkey, run:
kubectl get passkeys.vault.kio.kasten.io passkey1 -o yaml
Deleting Passkeys
You can delete existing Passkeys if they are no longer required. If only a single valid Passkey exists, it cannot be deleted.
kubectl delete passkeys.vault.kio.kasten.io passkey1