Multi-Cluster Access
For users to get access to K10 Multi-Cluster Manager, K10 Multi-Cluster access control can be configured.
Users first need access to clusters bootstrapped and available in the K10 Multi-Cluster Manager setup. Refer K10 Multi-Cluster User section for more information.
Configuring Access for Multi-Cluster Users
K10 allows users and/or groups to be bound to a list of clusters with
pre-defined K10ClusterRoles. This ensures, users and/or groups can be
given granular access for individual clusters.
K10 will handle any Kubernetes roles or bindings required to facilitate the access control.
Note
Because K10 handles access control, authentication domains for users/groups can be different on primary and secondary clusters.
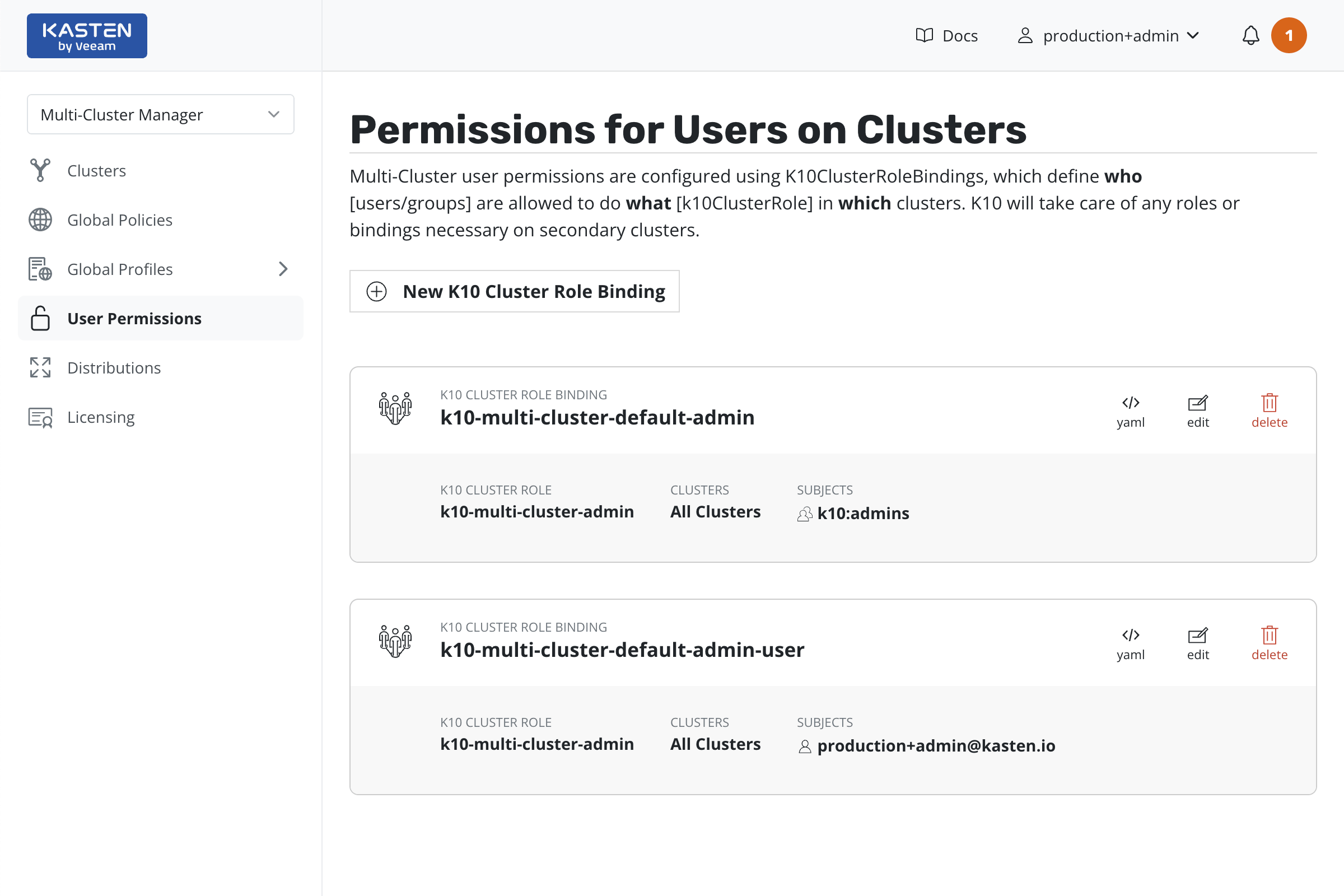
Admin users can add or update K10ClusterRoleBindings in the
K10 Multi-Cluster Manager dashboard.
K10ClusterRoleBindings
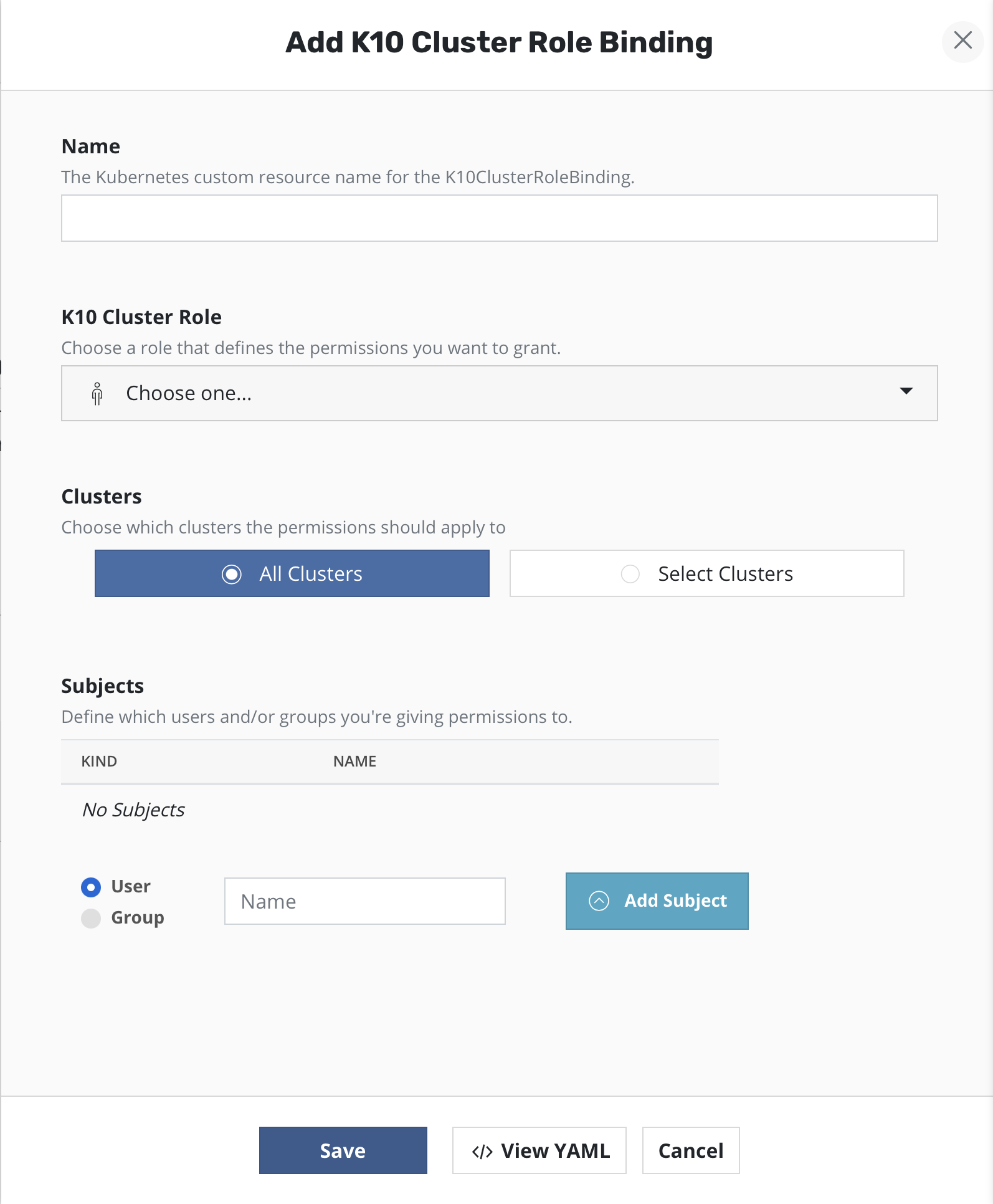
K10ClusterRoleBindings defines users/groups access to clusters.
One of the predefined K10ClusterRoles, k10-multi-cluster-admin,
k10-multi-cluster-basic or k10-multi-cluster-config-view, can
be selected.
Either all clusters or a list of clusters can be selected using name or a selector string.
List of users or groups can be added using fully qualified names.
The complete RBAC reference for K10ClusterRoleBindings can be found in
this section.