Installing Veeam Kasten on Google Cloud
Prerequisites
Before installing Veeam Kasten on Google Cloud's Google Kubernetes Engine (GKE), please ensure that the install prerequisites are met.
For a default GKE install, a volumesnapshotclass will need to be
created and annotated with k10.kasten.io/is-snapshot-class: "true".
To see how to create a volumesnapshotclass, refer to
this google documentation
Installing Veeam Kasten
Installing Veeam Kasten on Google requires two kinds of Service
Accounts. The first, documented below, is a Google Cloud Platform (GCP)
Service Account
(SA)
that grants access to underlying Google Cloud infrastructure resources
such as storage. The second, as mentioned above in the Prerequisites
section, is a Kubernetes Service Account that grants access to
Kubernetes resources and will be auto-created during the helm install
process or via Google Marketplace options.
It is advised to make sure that the necessary permissions are available before proceeding with the installation of Veeam Kasten. The process of granting permissions may vary depending on the chosen installation mode. It is important to follow the instructions relevant to the desired installation mode to ensure a smooth and successful installation of Veeam Kasten.
GCP Service Account Configuration
Veeam Kasten uses the Google Cloud Platform Service Account to
manage volumesnapshot in the GCP account. Therefore, the service
account needs to be assigned the
compute.storageAdmin
role.
Using the Default GCP Service Account
A GCP Service Account automatically gets created with every GKE cluster. This SA can be accessed within the GKE cluster to perform actions on GCP resources and, if set up correctly at cluster creation time, can be the simplest way to run the Kasten platform.
This SA configuration needs to be done at cluster creation time. When using the Google Cloud Console to create a new Kubernetes cluster, please select More Options for every node pool you have added. Search for Security in the expanded list of options and, under Access Scopes, select Set access for each API. In the list of scopes that show up, please ensure that Compute Engine is set to Read Write.
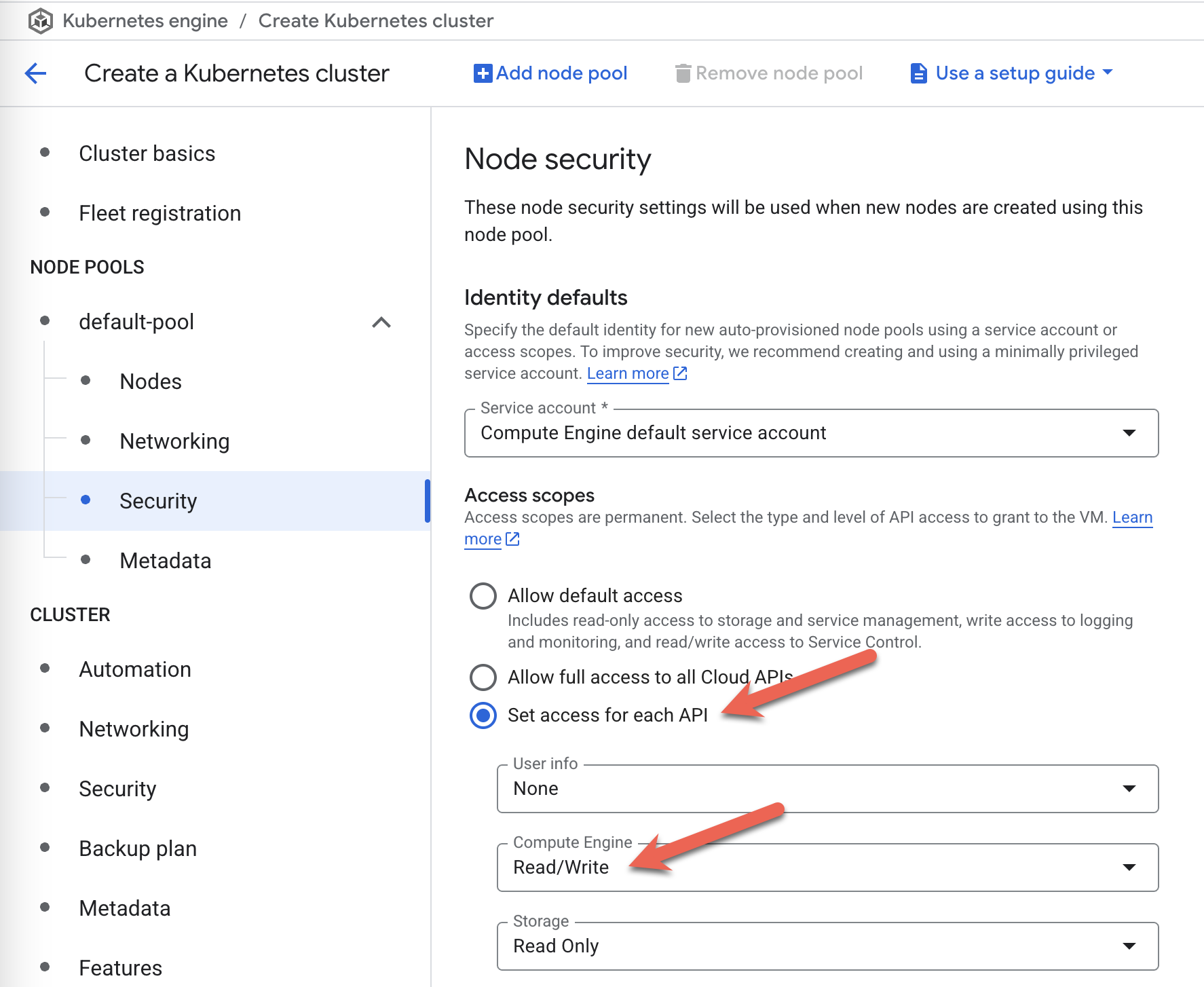
Using a Separate GCP Service Account
The preferred option for a Veeam Kasten install is to create and use a separate Google service account with the appropriate permissions to operate on the underlying Google Cloud infrastructure and then use that. For more details on how to create and use a separate service account, refer to the following links:
For information on adding the compute.storageAdmin role to a Google
Cloud Platform Service Account for the associated GCP project, refer to
this
link.
Service Account Key
Veeam Kasten requires a Service Account key for the GCP Service Account and the GCP Project ID associated with it.
Service Accounts for a Marketplace Install
If you are installing on Google via the Google Marketplace, you can elect to allow the marketplace install create a K10 service account as well as a reporting service account, although your user may require administrative privileges in IAM to do so. Alternatively, you can pre-create the service accounts by following these instructions to install.
Once the Service Accounts are created and the node pools are running, Veeam Kasten can then be installed by running the following install command:
$ helm install k10 kasten/k10 --namespace=kasten-io
To address any troubleshooting issues while installing Veeam Kasten on a Kubernetes platform using the Cilium Container Network Interface (CNI) setup, refer to this page. The page provides specific steps for resolving installation issues with Cilium CNI and Veeam Kasten compatibility.
Validating the Install
To validate that Veeam Kasten has been installed properly, the following
command can be run in Veeam Kasten's namespace (the install default is
kasten-io) to watch for the status of all Veeam Kasten pods:
$ kubectl get pods --namespace kasten-io --watch
It may take a couple of minutes for all pods to come up but all pods
should ultimately display the status of Running.
$ kubectl get pods --namespace kasten-io
NAMESPACE NAME READY STATUS RESTARTS AGE
kasten-io aggregatedapis-svc-b45d98bb5-w54pr 1/1 Running 0 1m26s
kasten-io auth-svc-8549fc9c59-9c9fb 1/1 Running 0 1m26s
kasten-io catalog-svc-f64666fdf-5t5tv 2/2 Running 0 1m26s
...
In the unlikely scenario that pods that are stuck in any other state, please follow the support documentation to debug further.
Validate Dashboard Access
By default, the Veeam Kasten dashboard will not be exposed externally.
To establish a connection to it, use the following kubectl command to
forward a local port to the Veeam Kasten ingress port:
$ kubectl --namespace kasten-io port-forward service/gateway 8080:80
The Veeam Kasten dashboard will be available at http://127.0.0.1:8080/k10/#/.
For a complete list of options for accessing the Kasten Veeam Kasten dashboard through a LoadBalancer, Ingress or OpenShift Route you can use the instructions here.