Application-Scoped Policies¶
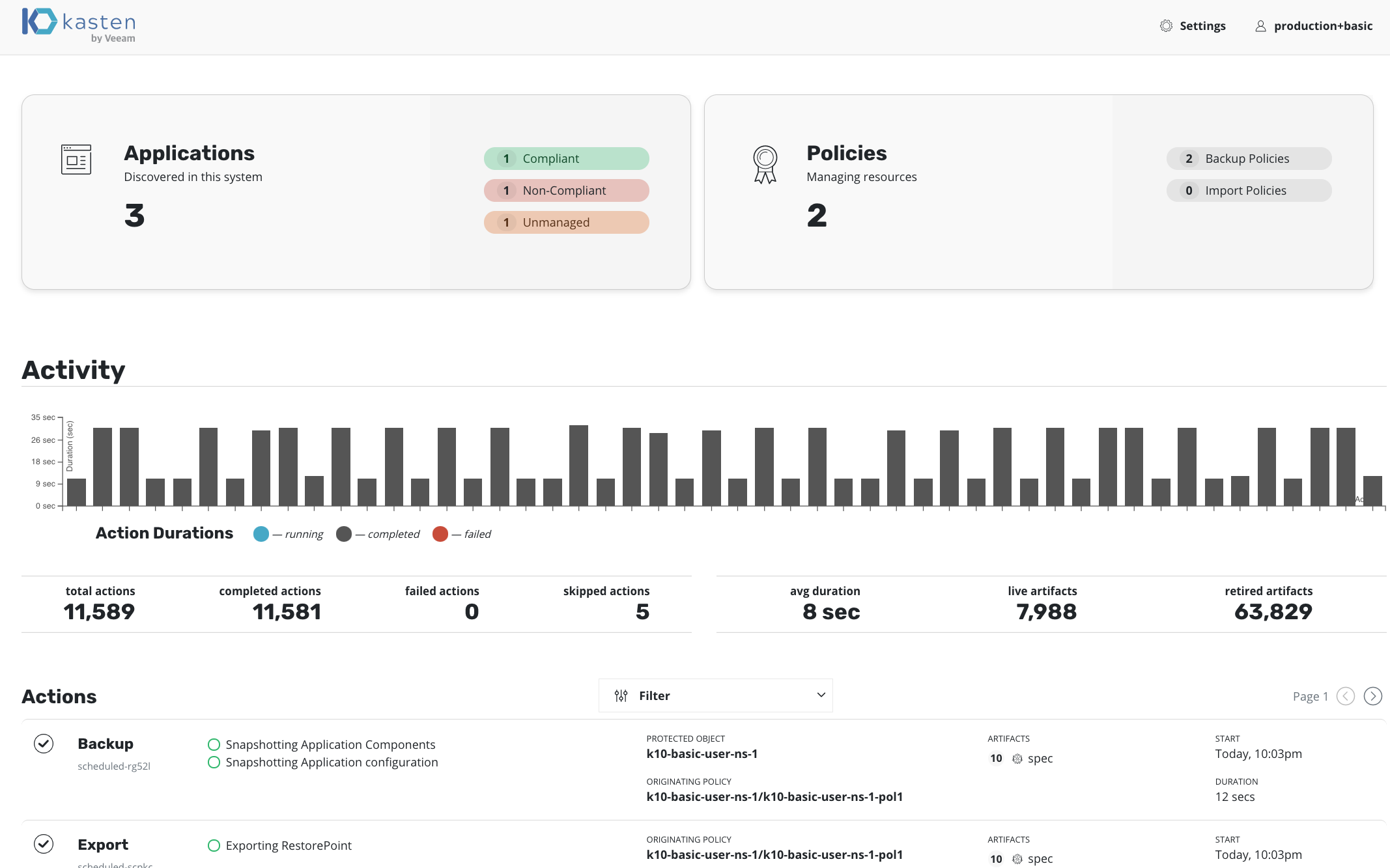
Users who are not administrators can create K10 policies in an application's namespace for protecting only that specific application. The image below shows the dashboard as viewed by a non-admin user who has access to policies.
For information about setting up RBAC for users of application-scoped policies, refer to this page.
Creating the Policy¶
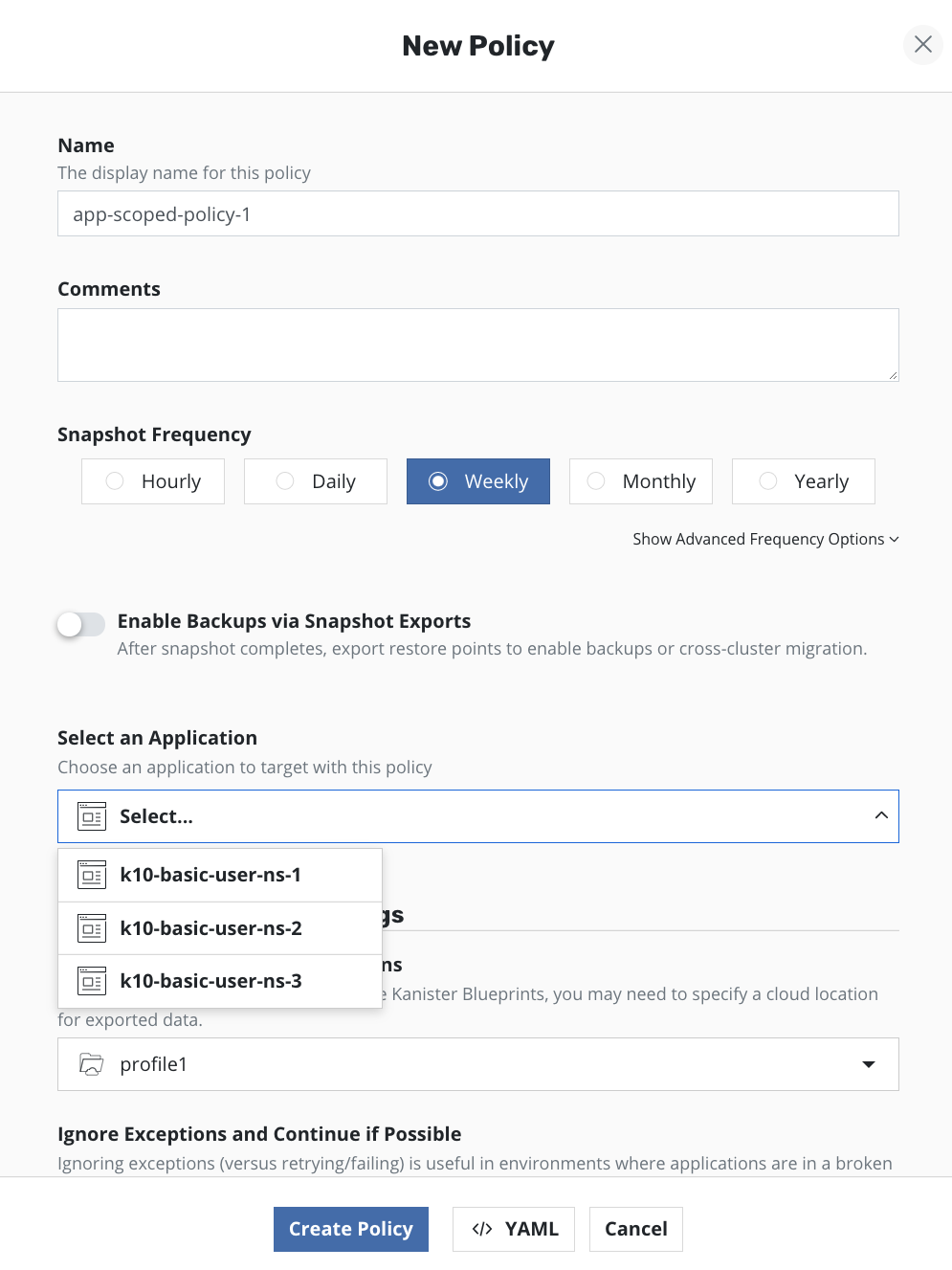
A user who does not have administrator privileges will see a different policy creation form compared to an admin user. The main difference is in the ability to select the applications that can be protected by such a policy. The image below shows that the user is allowed to only select a single application.
A K10 Policy resource is created in the application's namespace.
kind: Policy
apiVersion: config.kio.kasten.io/v1alpha1
metadata:
name: k10-basic-user-ns-1-pol1
namespace: k10-basic-user-ns-1
spec:
frequency: "@hourly"
subFrequency:
minutes:
- 0
- 30
- 55
hours:
- 0
weekdays:
- 0
days:
- 1
months:
- 1
retention:
hourly: 24
daily: 7
weekly: 4
monthly: 12
yearly: 7
selector:
matchExpressions:
- key: k10.kasten.io/appNamespace
operator: In
values:
- k10-basic-user-ns-1
actions:
- action: backup
- action: export
exportParameters:
frequency: "@hourly"
receiveString: exampleReceiveString
profile:
name: profile1
namespace: kasten-io
migrationToken:
name: k10-basic-user-ns-1-pol1-migration-token-n74p8
namespace: kasten-io
exportData:
enabled: true
retention: {}
Profiles¶
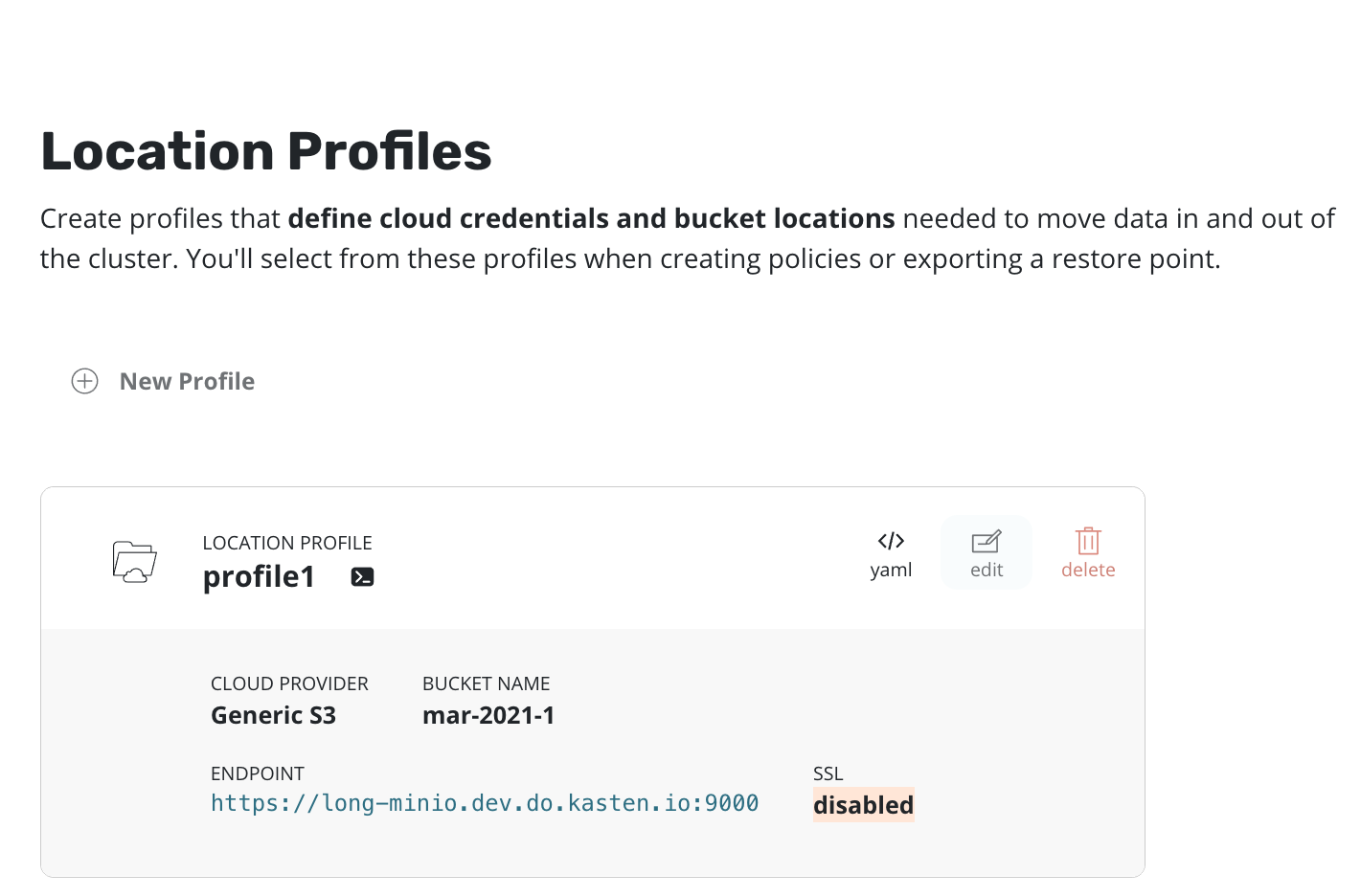
The users of application-scoped policies require read-only access to location profiles. They depend on the administrator for creation of profiles. The image below shows the profiles page as seen by such a user. The user can list/view the profiles that they have been given access to. But they cannot create, edit or delete them. Refer to this page for setting up RBAC to provide access to profiles in K10's namespace for non-admin users.
Backups¶
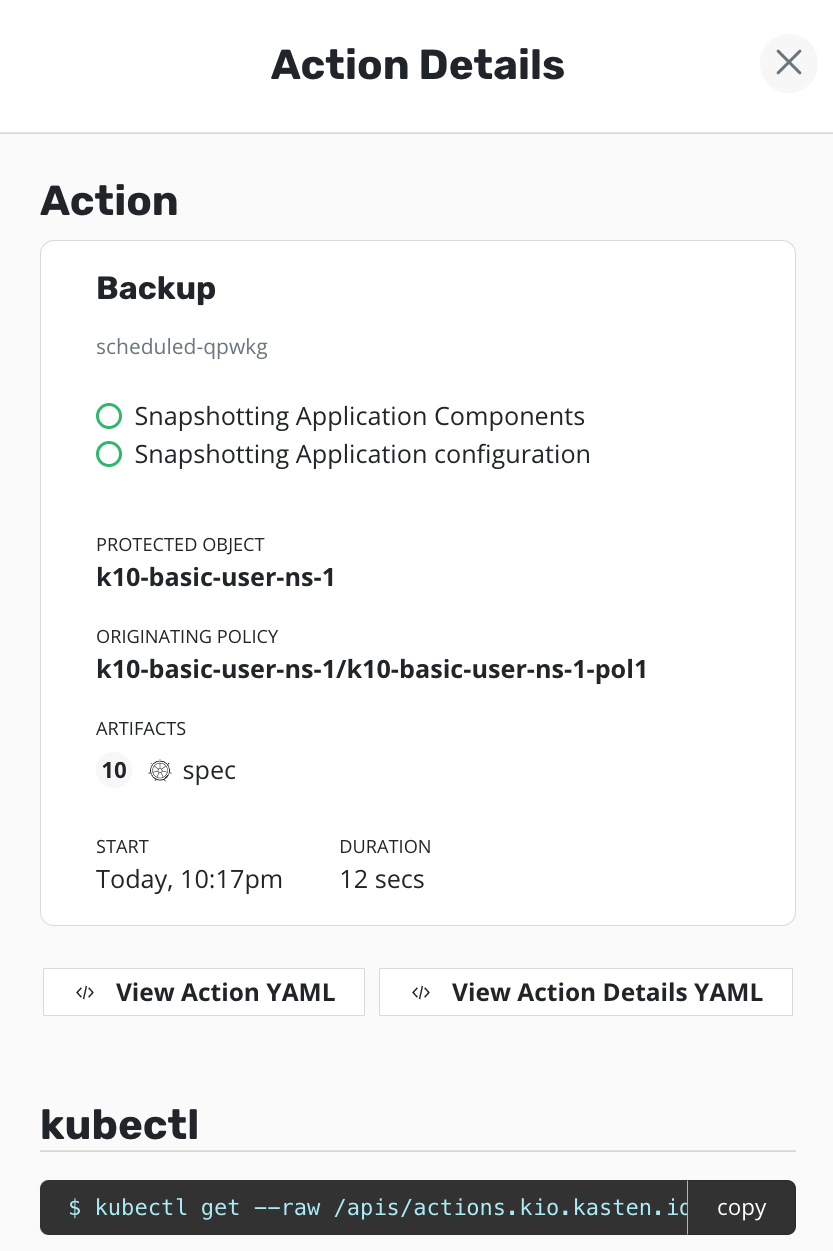
When the policy runs, the BackupActions and Restore Points will
be created in the application's namespace. The image below shows
a BackupAction. The originating policy indicates that the policy
named k10-basic-user-ns-1-pol1 in the namespace
named k10-basic-user-ns-1 created this BackupAction.
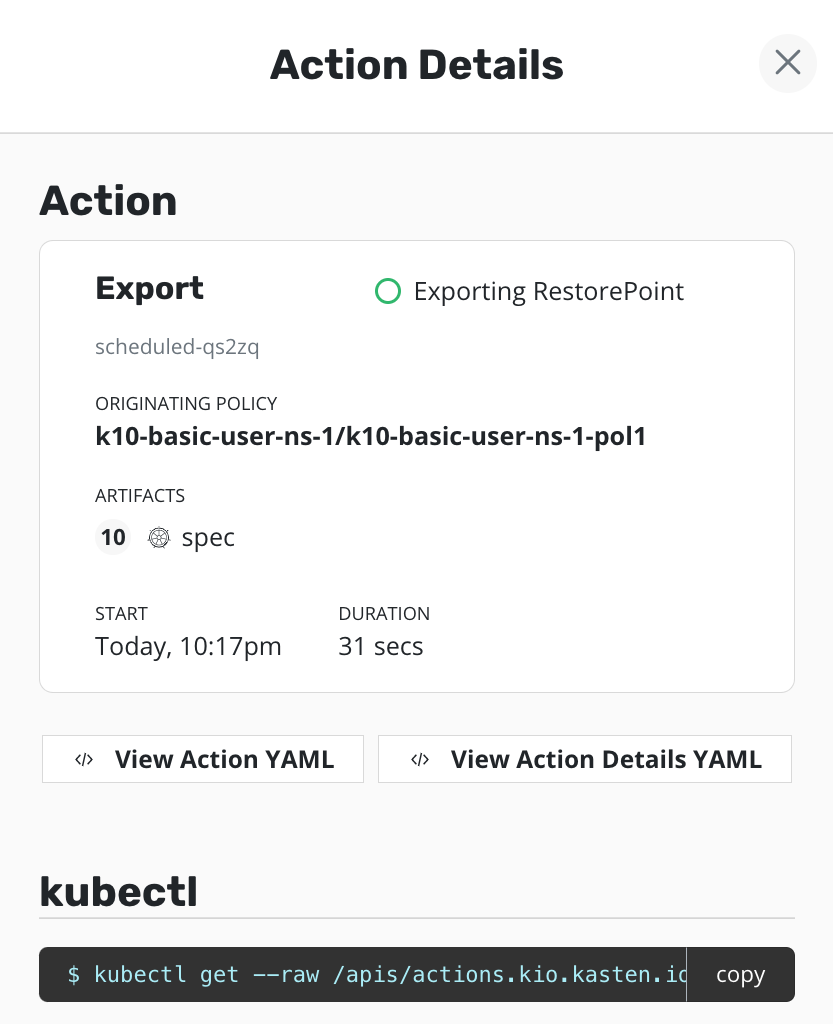
Exports¶
If the policy is configured to export Restore Points to object storage,
the ExportAction will be created in the application's
namespace. The image below show an ExportAction. The originating policy
indicates that the policy named k10-basic-user-ns-1-pol1 in the
namespace named k10-basic-user-ns-1 created this ExportAction.
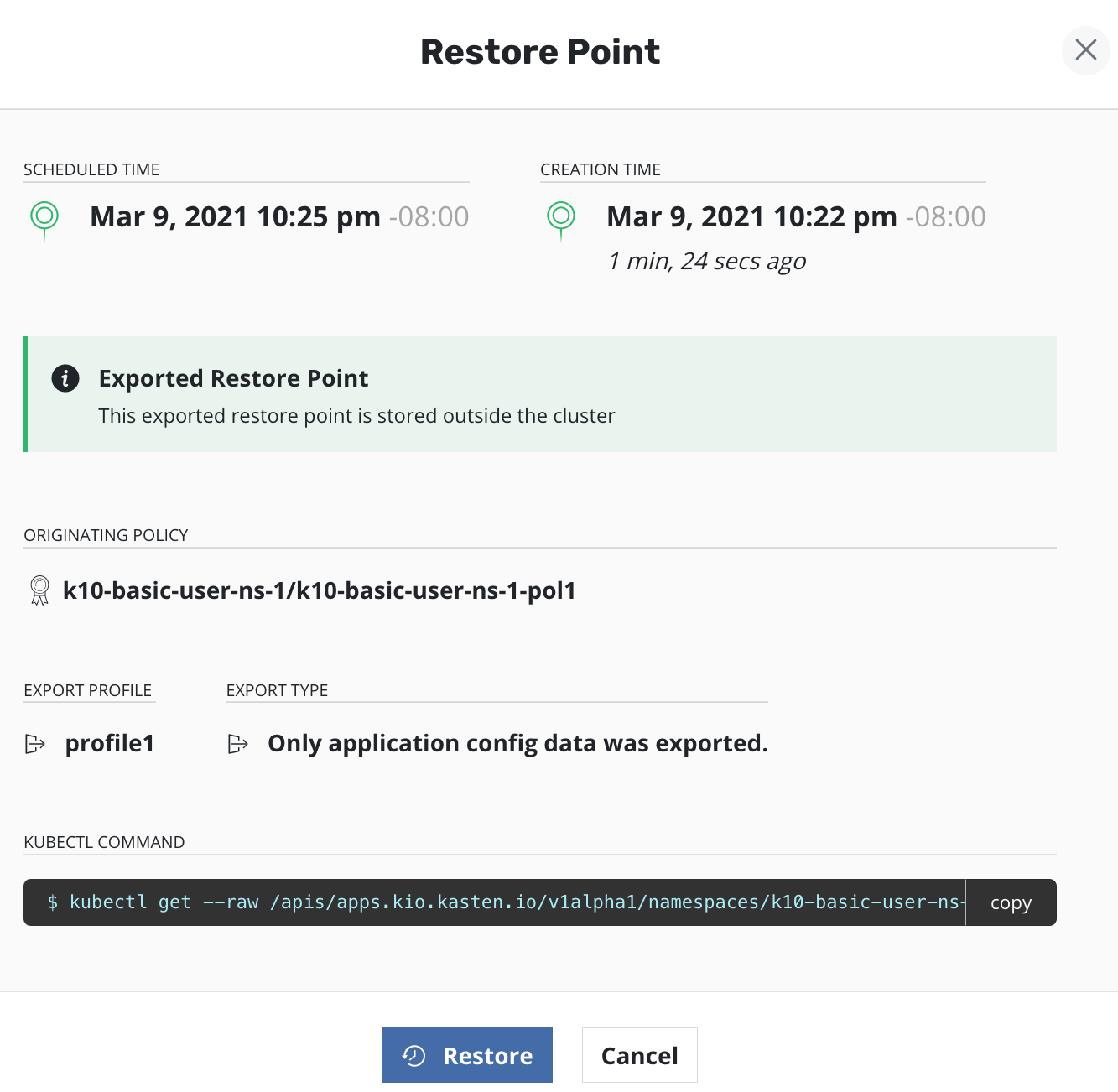
Restores¶
The non-admin user can restore the application using one of the Restore Points created by the application-scoped policy. This image below shows an exported Restore Point whose originating policy is an application-scoped policy.
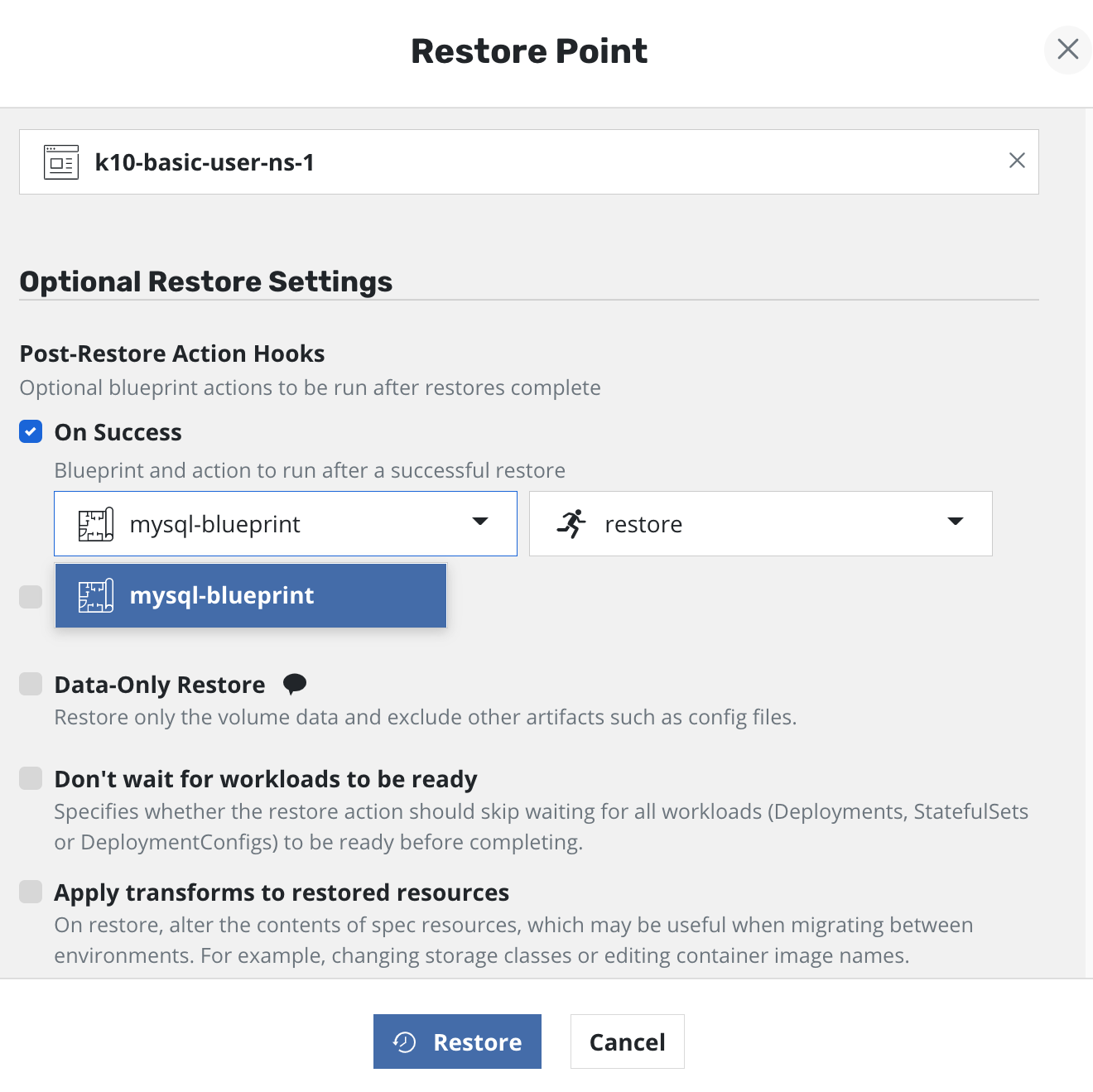
In the Optional Restore Settings section of the restore form, the user can select Kanister blueprint actions that will run after a successful restore. The users of application-scoped policies require read-only access to such blueprints. They depend on the administrator for creation of blueprints. Refer to this page for setting up RBAC to provide access to blueprints in K10's namespace for non-admin users.