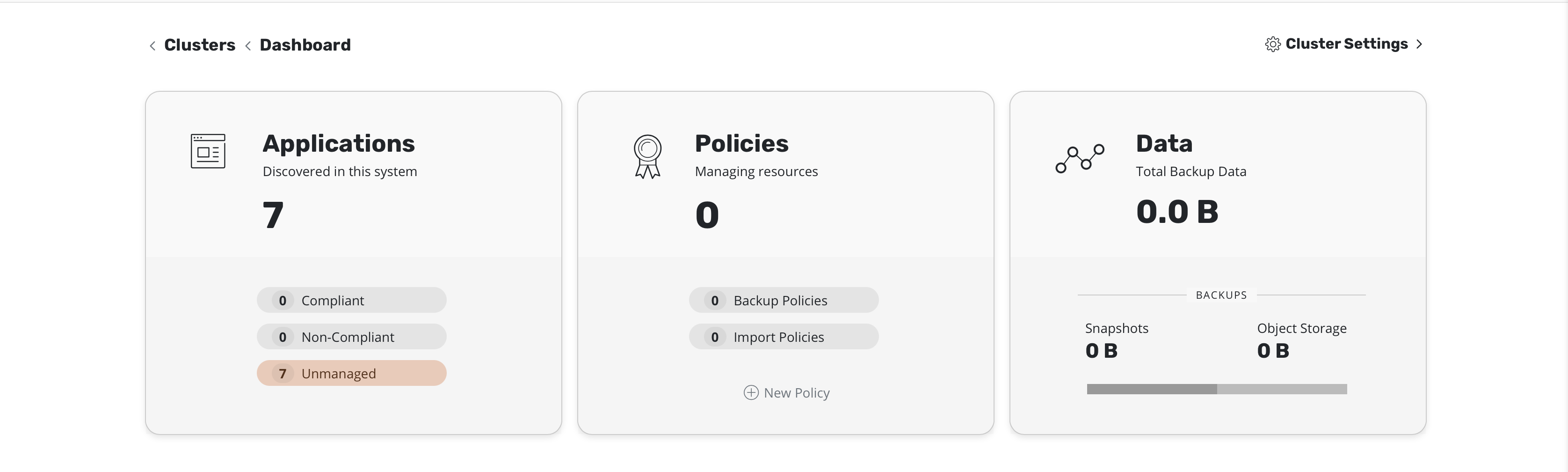
Dashboard Access¶
Once a primary cluster is configured for the K10 Multi-Cluster Manager features can be accessed via the K10 Dashboard.
Multi-Cluster Admins¶
The K10 Multi-Cluster Manager dashboard will be available at https://<URL to k10 gateway service>/k10/#/clusters for K10 exposed externally or http://127.0.0.1:<forwarding port>/k10/#/clusters for K10 exposed through kubectl port-forward during K10 install. Refer Dashboard Access for more information.
If a cluster is setup as primary, the K10 dashboard will have breadcrumbs that allow navigation to the K10 Multi-Cluster Manager dashboard.
For users to get admin access to the K10 Multi-Cluster Manager dashboard as well as other K10 Multi-Cluster features, additional role bindings may be required.
The k10-mc-admin ClusterRole is installed during K10 install/upgrade.
It grants admin users access to Distributions, Clusters, K10 Config, Secrets
and Multi-Cluster RBAC configurations in the K10 multi-cluster namespace.
During bootstrapping, K10 creates a RoleBinding for a default Group
k10:admins in the K10 multi-cluster namespace. Admin users can be added
to this Group and will be able to use the above k10-mc-admin ClusterRole.
Note
k10-mc-admin will be installed under the name <release_name>-mc-admin.
This ClusterRole is not configurable and is installed with K10.
You can also create role bindings for existing users or service accounts.
To bind the k10-mc-admin ClusterRole to a User, use the following command
$ kubectl create rolebinding <name> --clusterrole=k10-mc-admin \
--namespace=kasten-io-mc \
--user=<name>
To bind the k10-mc-admin ClusterRole to a ServiceAccount, use the following
command
$ kubectl create rolebinding <name> --clusterrole=k10-mc-admin \
--namespace=kasten-io-mc \
--serviceaccount=<serviceaccount_namespace>:<serviceaccount_name>
- The complete RBAC reference can be found in the
K10 Multi-Cluster RBAC section.
Multi-Cluster Users¶
For users who need access only to certain cluster-level operations but not the K10 Multi-Cluster Manager configurations, admins can configure users to have limited access control using K10 Multi-Cluster RBAC. Refer Multi-Cluster User Access for more information.